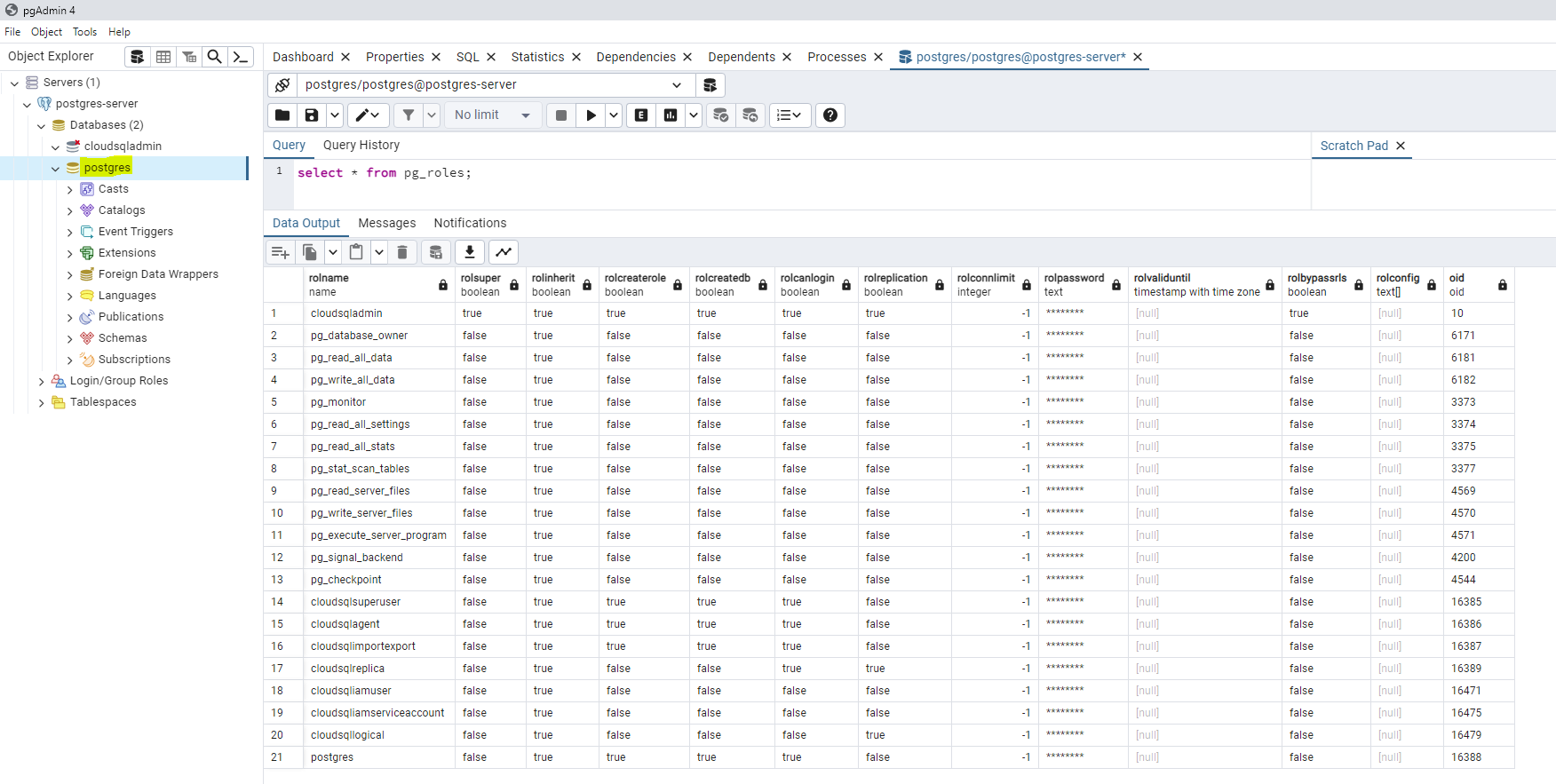
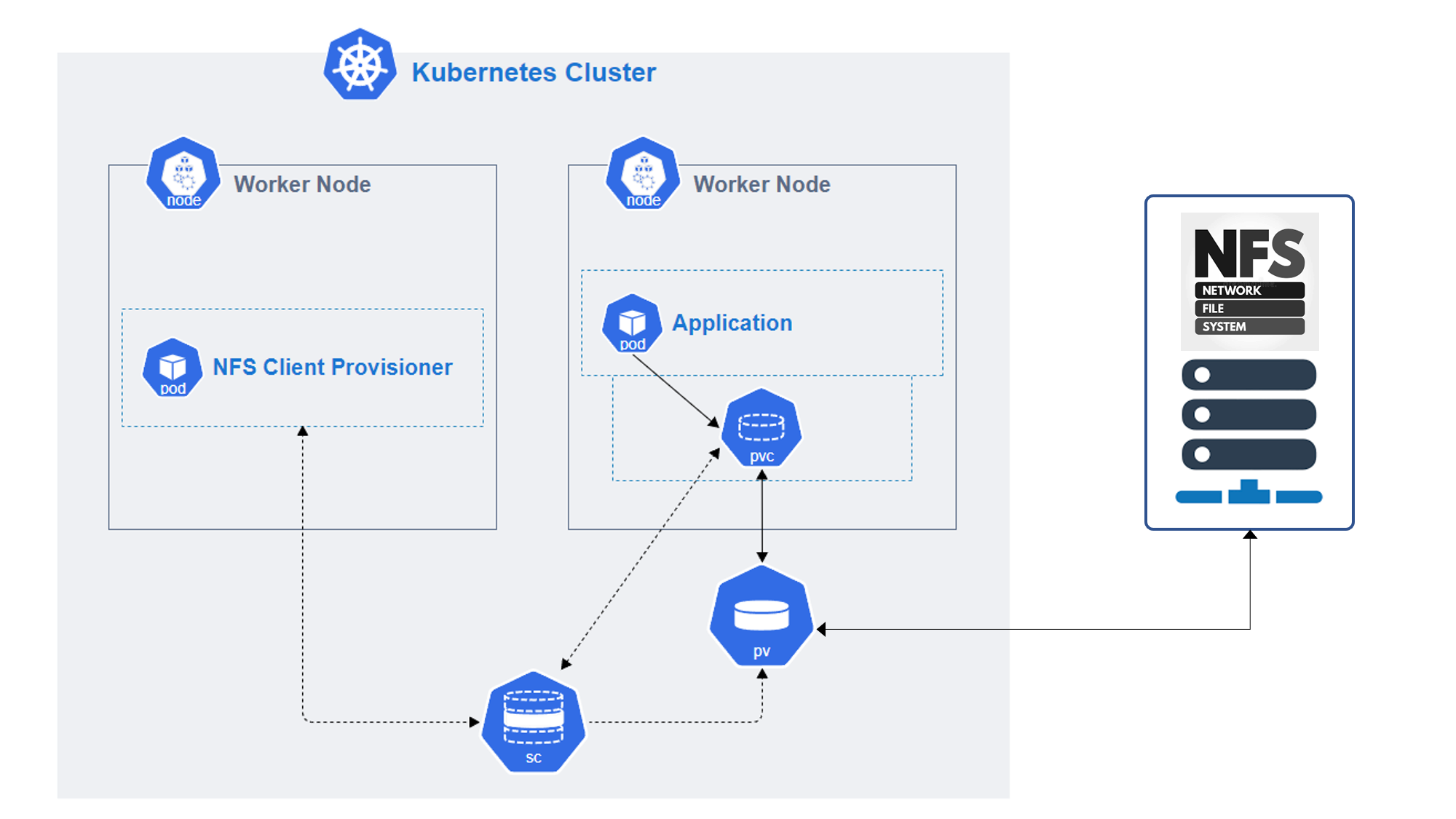
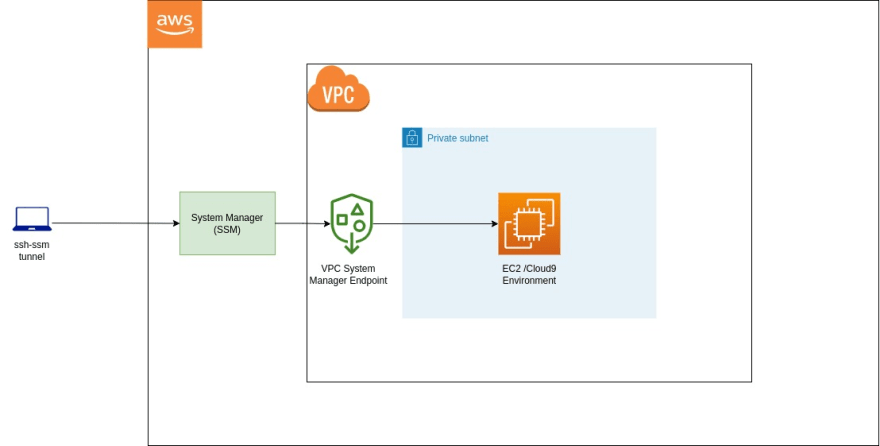
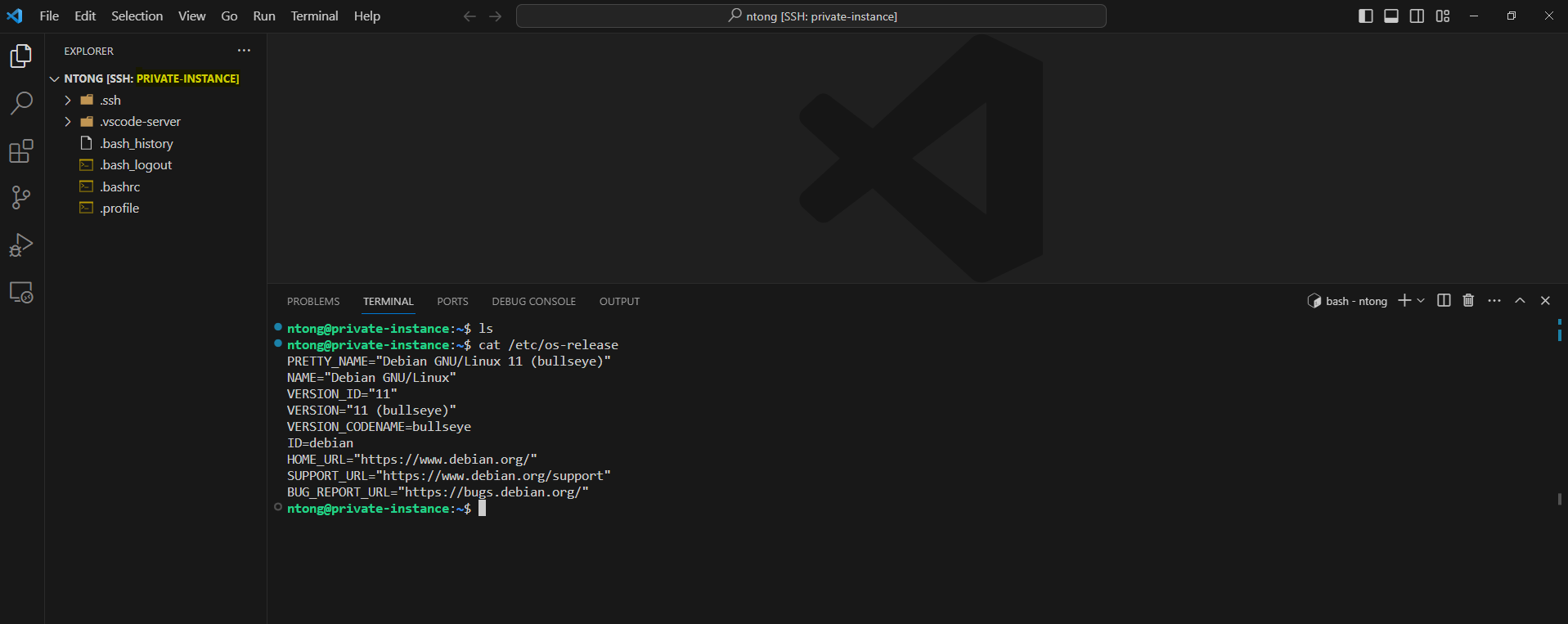
A virtual private network (VPN) is a type of private interconnected network.
VPNs are typically deployed to connect two or more trusted private networks to one another over an untrusted network (over the Internet).
Traffic is encrypted while traveling over the untrusted network to prevent eavesdropping or other attacks.
You may consider three types of gateway below when designing your hybrid network:
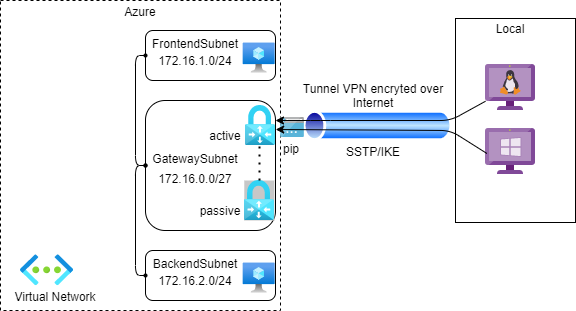
- Point-to-site (P2S) VPN: allows client computers in local to connect remotely to your network in Azure using IPSec/OpenVPN/SSTP protocols
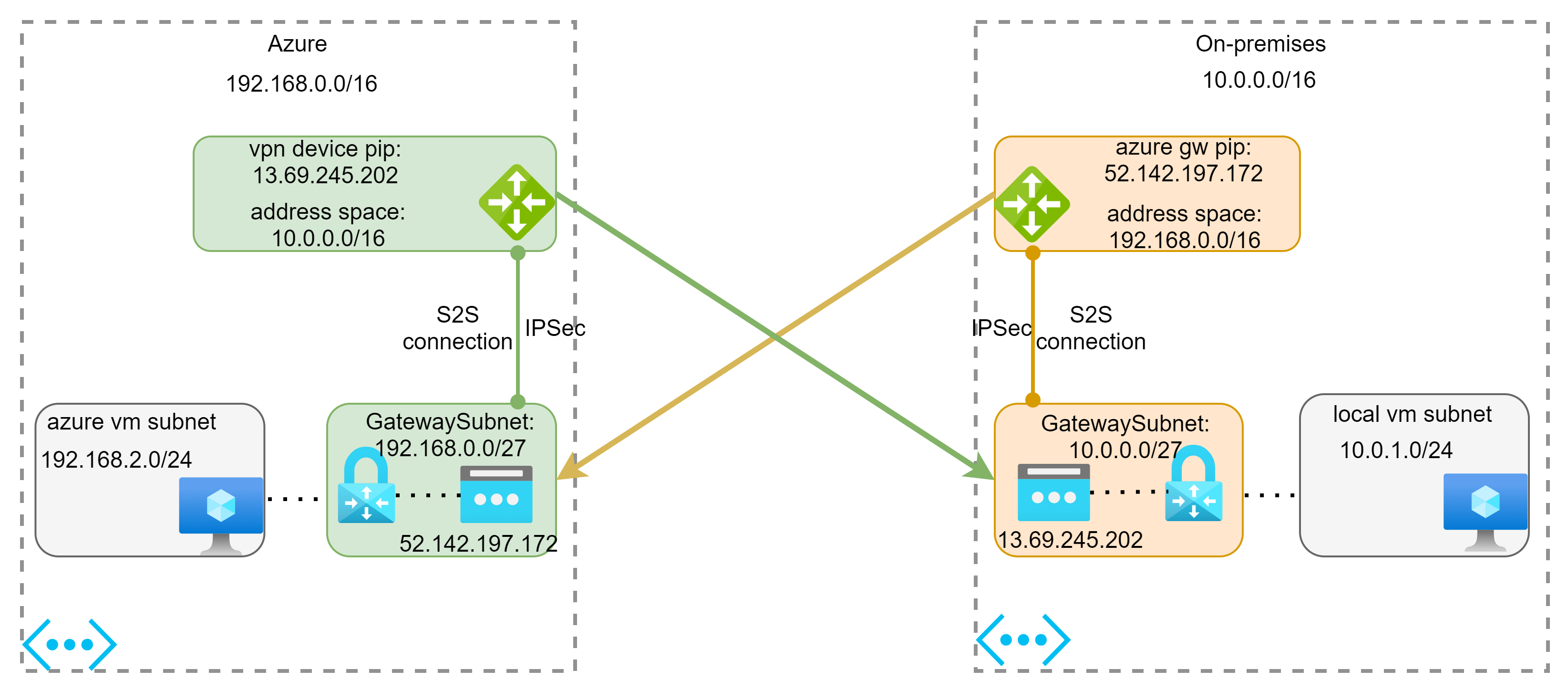
- Site-to-site (S2S) VPN: connect your on-premises networks to Azure through dedicated VPN devices or connect multiple virtual networks in Azure together. Protocols supported: IPSec/IKE
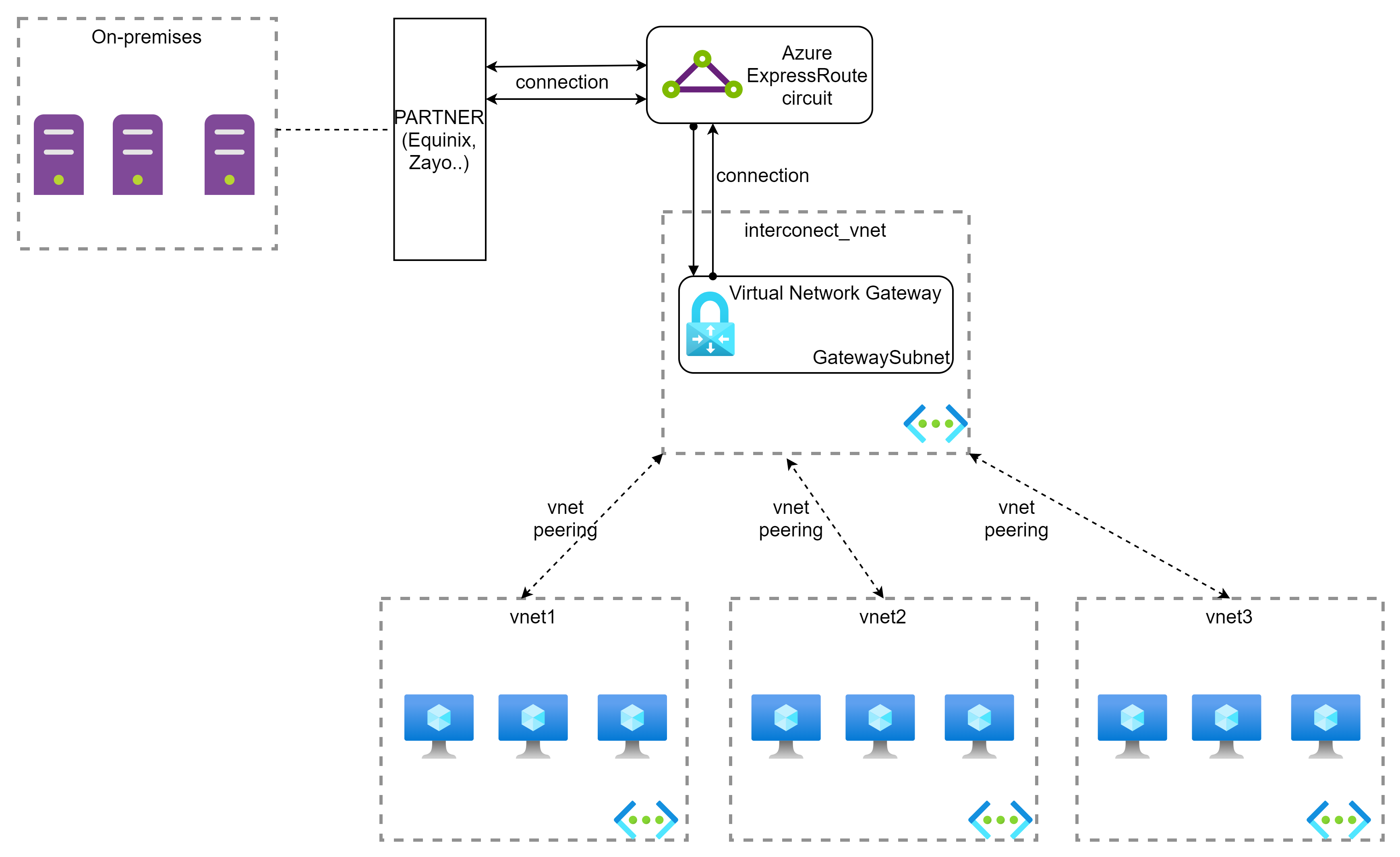
- Azure ExpressRoute: connect your on-premises networks to Azure over a private network. It means that your traffic will be not travel over the Internet.
In this first part, we will discuss the Point-to-Site VPN.
Part 2 (Site-to-Site VPN) available here.
[Read More]