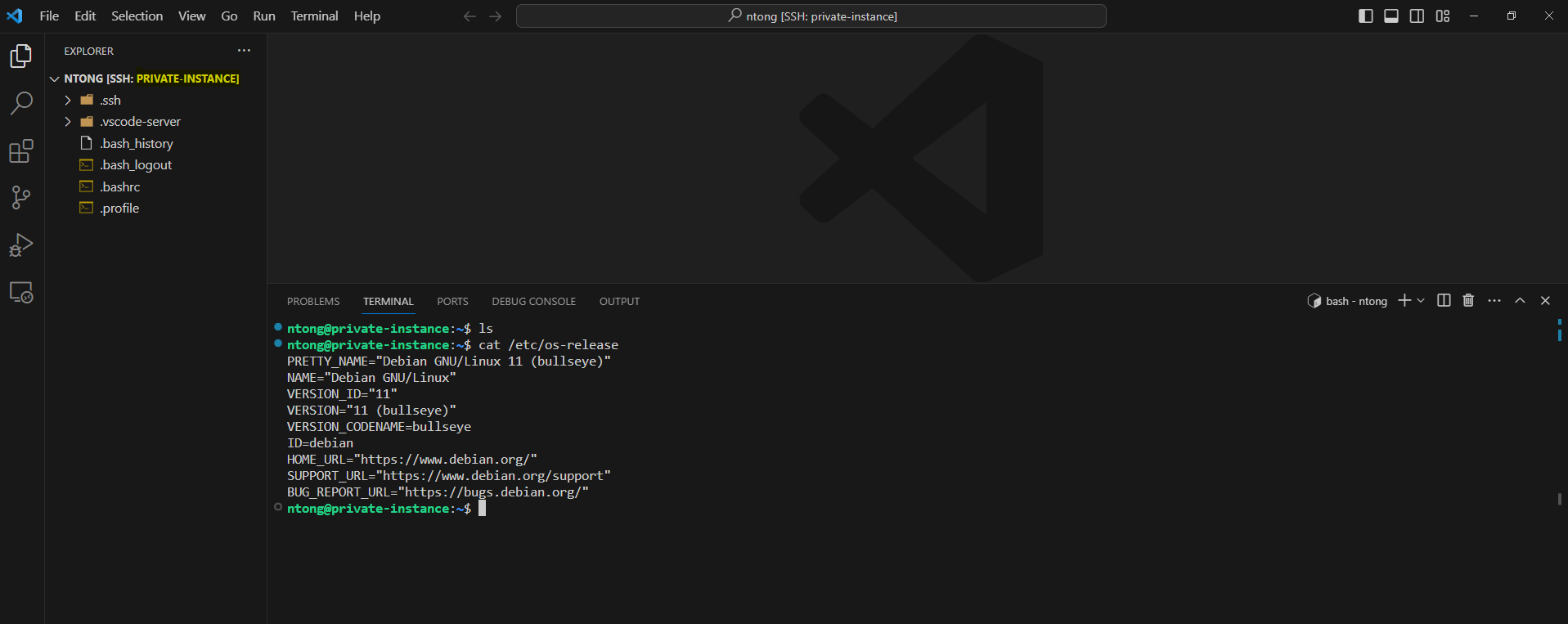
In this part, we will delve into the process of connecting to private instances using Visual Studio Code with Remote-SSH extension.
Google Cloud Platform
Prerequisites :
- Install Google Cloud SDK
- Attention: try to avoid spaces while choosing the folder location (for ex: “Cloud-SDK” instead of “Cloud SDK”)
- Install Remote-SSH extension for Visual Studio Code
Steps
- Setup gcloud by running the following command from your Visual Studio Code’s terminal:
gcloud config set project [PROJECT_ID]
gcloud config set compute/region [REGION]
gcloud config set compute/zone [ZONE_NAME]
# Optional: if the network is behind a proxy
gcloud config set proxy/type http
gcloud config set proxy/address [PROXY_IP]
gcloud config set proxy/port [PROXY_PORT]
- Authenticate to GCP and connect to private instance through iap. This command also generate a key pair named google_compute_engine if it doesn’t exists and then add the public key to the private instance. The private key is stored in local.
gcloud auth login
gcloud compute ssh [VM_NAME] --tunnel-through-iap
- Generate ssh config for VSCode
gcloud compute ssh [VM_NAME] --tunnel-through-iap --dry-run
- Add new entry to ssh config and replace the following placeholders using output from the dry-run command above
Host [VM_NAME]
HostName compute.XXXXXXXXXXXXX
IdentityFile C:\Users\[USER]\.ssh\google_compute_engine
ProxyCommand C:\Users\[USER]\AppData\Local\Programs\Python\Python311\python.exe -S C:\Users\[USER]\AppData\Local\Google\google-cloud-sdk\lib\gcloud.py compute start-iap-tunnel [VM_NAME] 22 --listen-on-stdin --project=[PROJECT_ID] --zone=[ZONE_NAME] --verbosity=warning
User [USER]
* [VM_NAME]: private instance name
* HostName: the hostname provided by the dry-run command with format USER@HOSTNAME
* [USER]: the user provided by the dry-run command with format USER@HOSTNAME
* [PROJECT_ID]: gcp project id
* [ZONE_NAME]: zone on which the vm is created
- Connect to private instance using Remote-SSH extension from Visual Studio Code

Amazon Web Services
Prerequisites :
- Install AWS CLI
- Install Session Manager plugin for the AWS CLI
- Install Remote-SSH extension for Visual Studio Code

Steps
- Authenticate to AWS from VSCode’s terminal
- Generate a ssh key pair for EC2 instance and then extract the public key from the private key
aws ec2 create-key-pair --key-name ec2 --key-type rsa --key-format pem --query "KeyMaterial" --output text > ec2.pem
chmod 400 ec2.pem
ssh-keygen -y -f ec2.pem > ec2.pub
- Connect to EC2 instance using Session Manager and then add public key ec2.pub to the instance at the location /home/ec2-user/.ssh/authorized_keys. Change the connected user to ec2-user if necessary:
sudo -i -u ec2-user
- Add new entry to ssh config
Host ssm-private-ec2
IdentityFile C:\Users\[USER]\.ssh\ec2.pem
HostName [EC2_INSTANCE_ID]
User ec2-user
Port 22
ProxyCommand aws ssm start-session --target %h --document-name AWS-StartSSHSession --parameters portNumber=%p
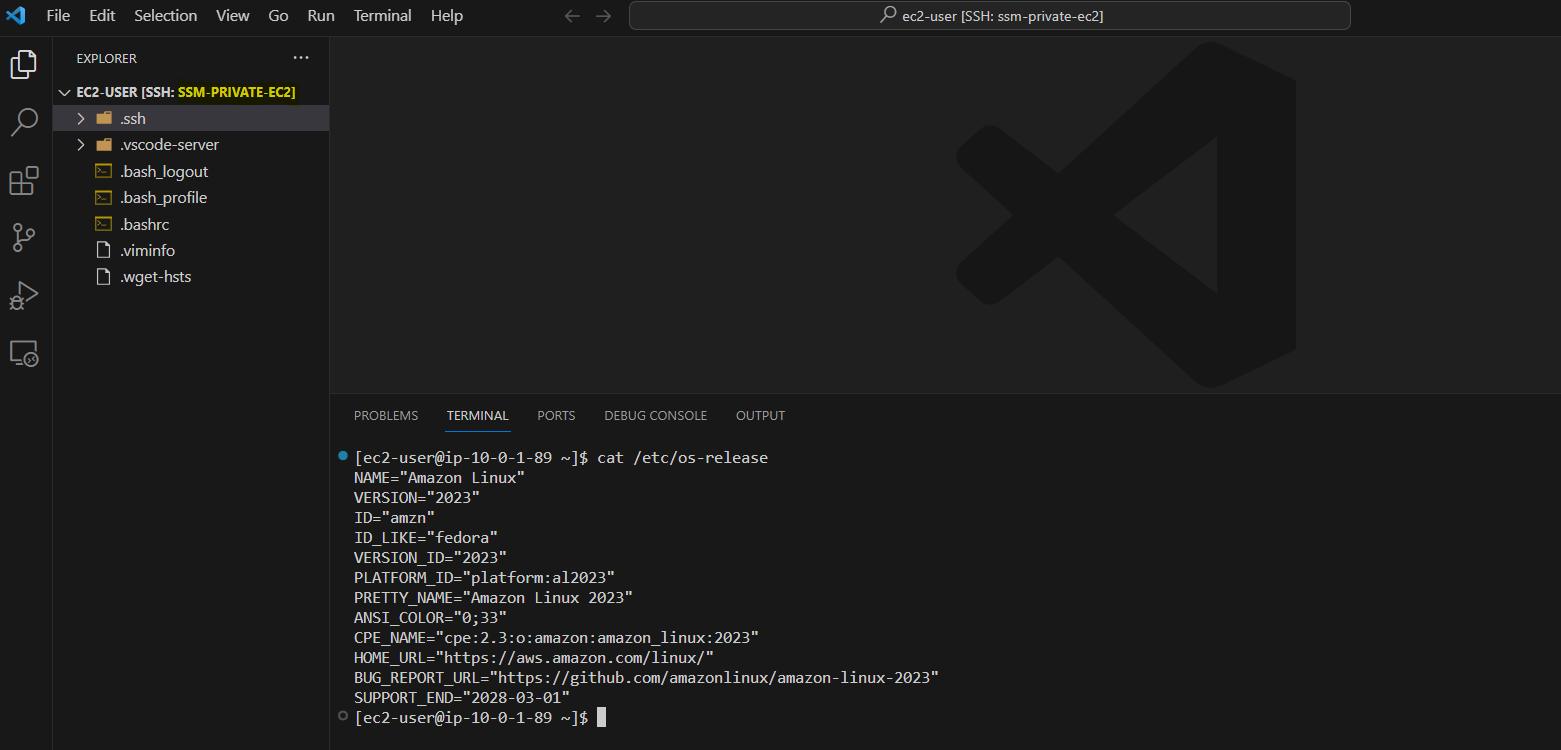
- Connect to private EC2 using Remote-SSH extension from Visual Studio Code
Azure
In order to connect to private virtual machine using Azure Bastion and Visual Studio Code, the Azure Bastion’s SKU Standard is required.
Azure Bastion SKU Developer and Basic are not supported this feature yet.
Prerequisites :
- Azure Bastion, tier Standard
- Install Azure CLI
- Install Remote-SSH extension for Visual Studio Code

Steps
- Enable feature Native client support on Azure Bastion

- Create a SSH tunnel via Azure CLI
az login --use-device-code -o none
az network bastion tunnel -n [AZURE_BASTION_NAME] -g [RESOURCE_GROUP_NAME] --target-resource-id [VM_RESOURCE_ID] --resource-port 22 --port 2222
* VM_RESOURCE_ID's format should be: /subscriptions/[SUBSCRIPTION_ID]/resourceGroups/[RG_NAME]/providers/Microsoft.Compute/virtualMachines/[VM_NAME]

- Add new entry to ssh config
Host azure-tunnel-local
IdentityFile C:\\Users\\[USER]\\.ssh\\id_rsa
HostName 127.0.0.1
User azureuser
Port 2222
StrictHostKeyChecking=No
- Connect to private vm from Visual Studio Code via the tunnel created earlier

Reference
- Developing on remote VM via VSCode using Google Cloud’s IAP
- Setup vscode ssh remote to a private EC2 instance via ssm
- Accessing AKS private clusters with Azure Bastion and VS Code